Dockle
It is one of the DevSecOps tools which detects the docker image Vulnerabilities and supports the CIS benchmarks.
Before pushing into the container registry, we need to make sure the image will be CIS benchmark standards.
Dockle has 5 check levels.
| LEVEL | DESCRIPTION |
| FATAL | Be practical and prudent |
| WARN | Be practical and prudent, but limited uses (even if official images) |
| INFO | May negatively inhibit the utility or performance |
| SKIP | Not found target files |
| PASS | Not found any problems |
Comparison
| Dockle | Hadolint | Docker Bench for Security | Clair | |
| Target | Image | Dockerfile | Host Docker Daemon Image Container Runtime |
Image |
| How to run | Binary | Binary | ShellScript | Binary |
| Dependency | No | No | Some dependencies | No |
| CI Suitable | ✓ | ✓ | x | x |
| Purpose | Security Audit Dockerfile Lint |
Dockerfile Lint | Security Audit Dockerfile Lint |
Scan Vulnerabilities |
Installation:
Create a new task to download and unzip the dockle.
– export VERSION=$(curl –silent “https://api.github.com/repos/goodwithtech/dockle/releases/latest” | grep ‘”tag_name”:’ | sed -E ‘s/.*”v([^”]+)”.*/\1/’)
– wget https://github.com/goodwithtech/dockle/releases/download/v${VERSION}/dockle_${VERSION}_Linux-64bit.tar.gz
– tar zxvf dockle_${VERSION}_Linux-64bit.tar.gz
Scan the image by using below command
Dockle –f json –o results imagename:tag
Here output save in results.
To see the results, run the below command
Cat results
Note: CIS Benchmarks is the product of a community consensus process and consists of secure configuration guidelines developed for docker.
| CODE | DESCRIPTION | LEVEL※ |
| CIS’s Docker Image Checkpoints | ||
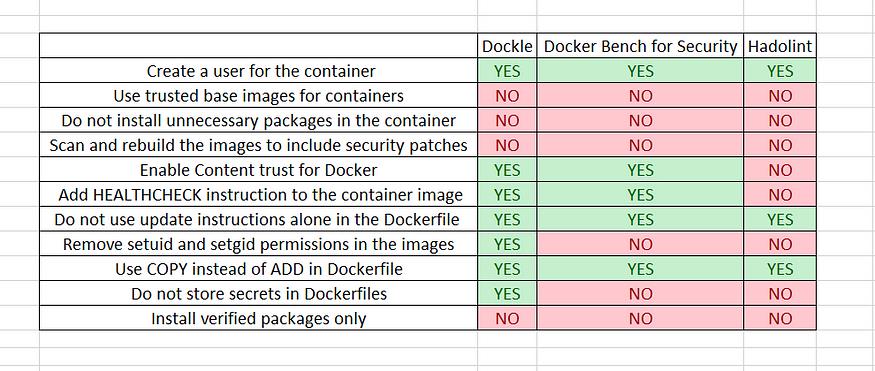
| CIS-DI-0001 | Create a user for the container | WARN |
| CIS-DI-0002 | Use trusted base images for containers | FATAL |
| CIS-DI-0003 | Do not install unnecessary packages in the container | FATAL |
| CIS-DI-0004 | Scan and rebuild the images to include security patches | FATAL |
| CIS-DI-0005 | Enable Content trust for Docker | INFO |
| CIS-DI-0006 | Add HEALTHCHECK instruction to the container image | WARN |
| CIS-DI-0007 | Do not use update instructions alone in the Dockerfile | FATAL |
| CIS-DI-0008 | Confirm safety of setuid and setgid files | INFO |
| CIS-DI-0009 | Use COPY instead of ADD in Dockerfile | FATAL |
| CIS-DI-0010 | Do not store secrets in Dockerfiles | FATAL |
| CIS-DI-0011 | Install verified packages only | INFO |
| Dockle Checkpoints for Docker | ||
| DKL-DI-0001 | Avoid sudo command | FATAL |
| DKL-DI-0002 | Avoid sensitive directory mounting | FATAL |
| DKL-DI-0003 | Avoid apt-get upgrade, apk upgrade, dist-upgrade | FATAL |
| DKL-DI-0004 | Use apk add with –no-cache | FATAL |
| DKL-DI-0005 | Clear apt-get caches | FATAL |
| DKL-DI-0006 | Avoid latest tag | WARN |
| Dockle Checkpoints for Linux | ||
| DKL-LI-0001 | Avoid empty password | FATAL |
| DKL-LI-0002 | Be unique UID/GROUPs | FATAL |
| DKL-LI-0003 | Only put necessary files | INFO |
